Organizational Security Management Training
At Nawetti Security, we are involved in:
Development of risk analyses, management and technical risks control.
Development and management of organizational security policies.
Development and management of organizational security procedures.
Drawing-up of organizational security plans and protocols.
Development of an emergency response plan.
Organizational security follow-up and evaluation schemes.
Certification and awards for best organizational security practices.
Individual Security Management Training
Capacity building in assessing individual vulnerabilities and strengths.
Development of individual security plans.
Capacity building in psychological, moral and physical in recovery plans.
Security incidents and consequences management plans.
Specific Security Management Training
Our specific security training reflects to individuals and/or their organizations operating within specific risky contexts and situations. It targets those persons and organizations that are under recurrent risks and threats due to their work in service for the well-being of others.
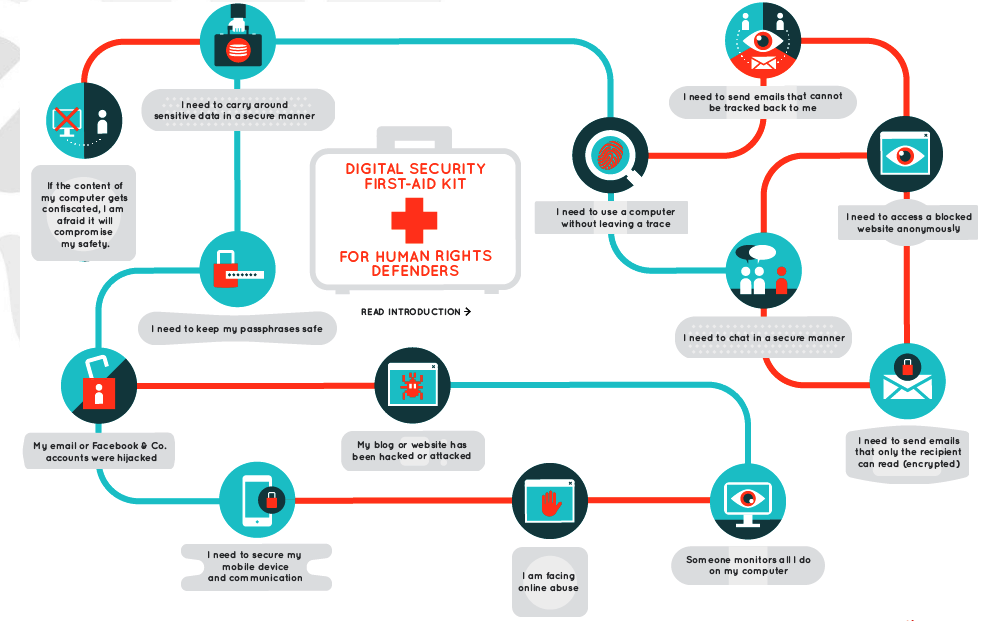
For Human Rights Defeneders (HRDs and Journalists)
Secured and effective data collection, processing and keeping techniques.
Secured and effective advocacy management procedures and opportunities targeting local, national, regional and global impact.
Pre-work space and context evaluation prior to engagements.
Securing networks and establishing purpose and supportive relationships.
Identification and analyses of work risks, threats and decisions to engage.
Activism control impacts against extremism and harmful consequences.
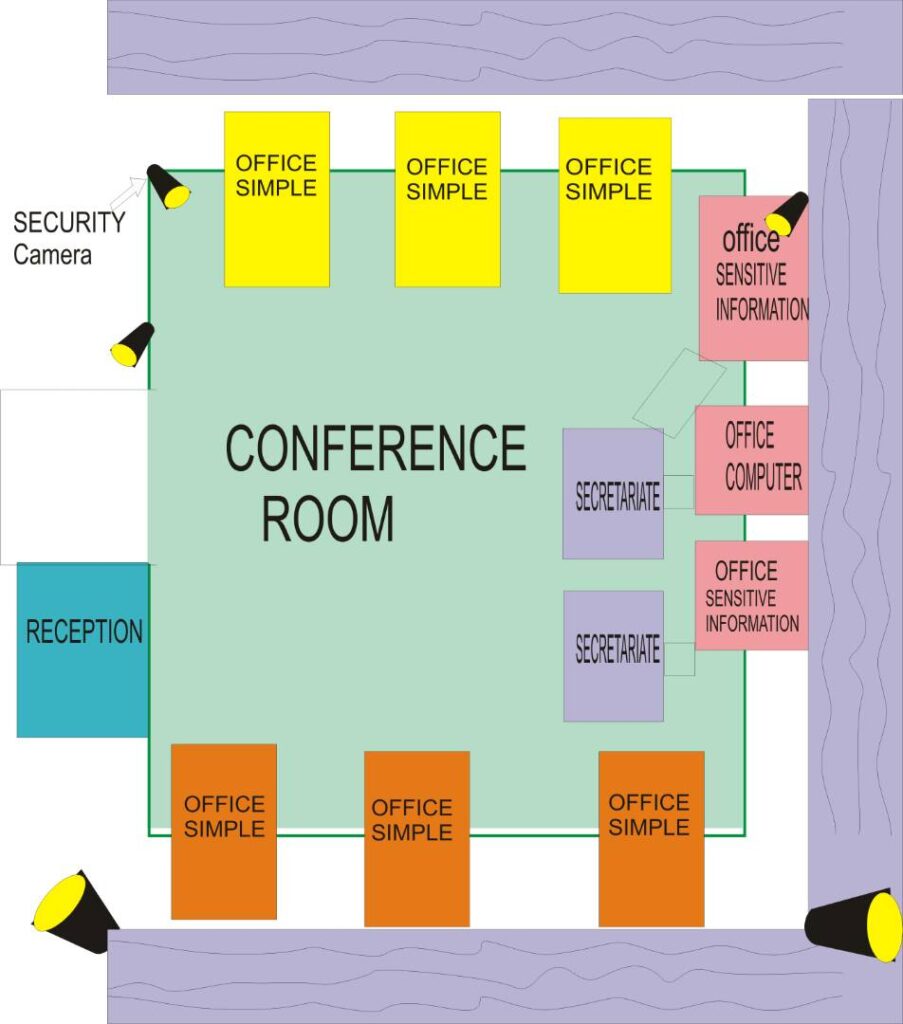
The Clergy and Other Susceptible Target Public Figures
Capacity building in assessing individual vulnerabilities and strengths.
Assessment of work objectives, relationships and third-party interests.
Risk analyses on work and leisure spaces, places and travels.
Development of individual security plans and organizational coverage procedures.
Capacity building in psychological, moral and physical in recovery plans.
Security incidents and consequences management plans.